Cloud Detection and Response
Detect, Investigate and Respond to Cloud Threats
Wiz collects cloud events and alerts from multiple providers, including AWS CloudTrail, Azure Activity Logs, GCP Cloud Audit Logs, and Amazon GuardDuty. It provides context for the risks identified by the Wiz Security Graph and detects suspicious events and threats via rules continuously updated by Wiz Research. You can extend the agentless malware scanning with custom feeds and collect samples, workload logs, and other forensics from cloud workloads. Built-in dynamic scanning validates external exposures, simulating what a potential attacker sees from outside your environment.
The Wiz Way
Contextualize Detection & Response
See your cloud activities come to life. Monitor your resources, their actions, and access across the environment in order to analyze threats in context so that you can prioritize, investigate, and respond quickly to the right risks.
Contextualize Threats
Correlate cloud threats with the underlying cloud architecture, and instantly understand the network, identity, workload, and data context associated with each risk.
Monitor Cloud Activity
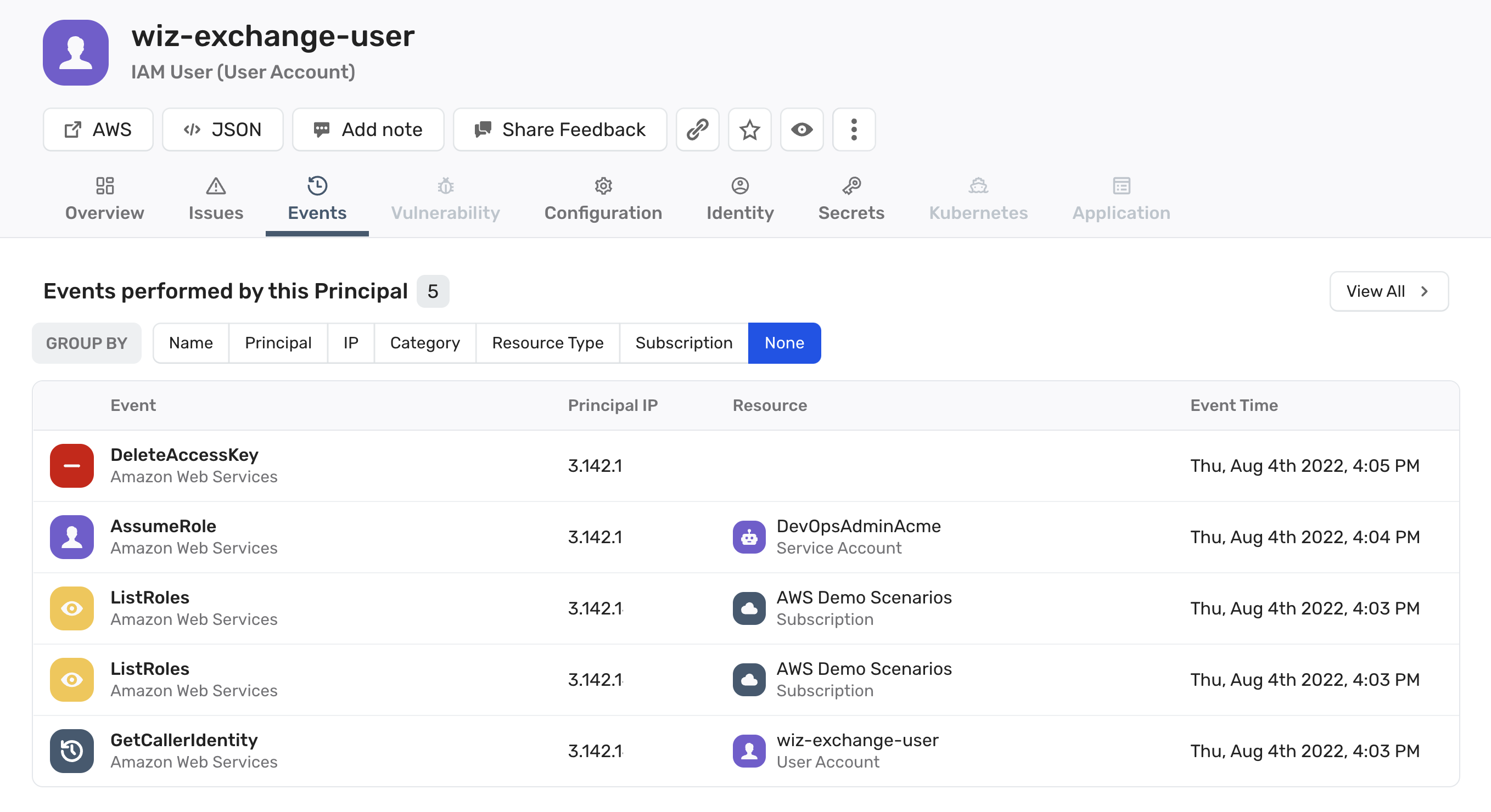
Monitor human identities, machine identities and third parties across your cloud environment and quickly investigate and understand any action with full Security Graph context.
Cloud-Native Incident Response
Utilize out-of-the-box response playbooks that are built to allow your team to investigate and isolate affected resources using cloud-native capabilities.
Threat Hunting
Investigate any event: Allow cloud builders to view activities and events their cloud environment, then investigate them in the context of their infrastructure. This allows security teams to easily manage and provide visibility to any team or member. Correlate cloud resources: Wiz allows security personnel and analysts to see each cloud event directly connected to the user or machine identity who performed it and the resource it was performed on. This automatic correlation makes it much easier to analyze and understand the cloud, network, IAM, and workload context in one place. Architecture context: Inspect threats and activities based on their context instead of predefined resources that continuously change. Define the search logic, then let Wiz connect everything else.
Go Beyond Threats
Prioritize with risk: Overlay the detections with the underlying infrastructure and risk context. Address the threats that affect the weakest or most valuable resources to focus cloud defenders’ efforts. Investigate with the graph: Quickly understand the impact of each detection by correlating it on the Wiz Security Graph with associated network, identity, or exposed secrets risks that may jeopardize your environment. Respond: Leverage playbooks that allow teams to act at scale across clouds to gather relevant information or isolate resources and harden the environment.
Getting started is easy
Complete security for AWS, Azure, GCP, OCI, Alibaba Cloud, Kubernetes, and Openshift. Start securing your cloud with a 5 minute agentless install. Meet your new partner in cloud security.